10 most dangerous viruses of all time
Computer viruses have long been a nightmare of all trades that involve computers. Here is a list of the 10 scariest computer viruses of all time.
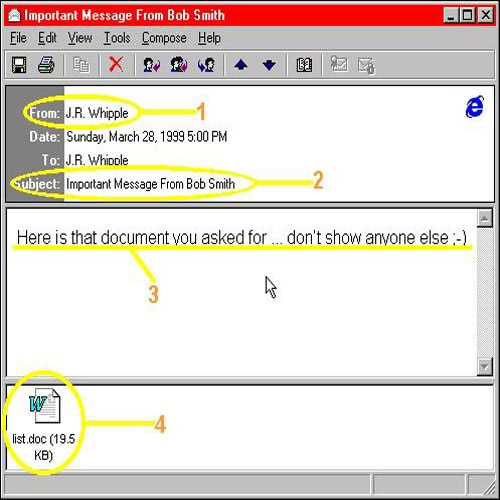
Melissa. In the spring of 1999, a man named David L.Smith created a computer virus based on the Microsoft Word command. This virus can spread through e-mails, called Melissa - the name of a famous dancer in Florida. This virus entices users to open a file with the accompanying message: 'This is the document you need, don't give it to anyone' . Once activated, the virus automatically duplicates and sends 50 others to your email address list, causing the email network to be blocked. According to FBI documents, the virus devastated the network of private and government networks. This is the first computer virus to attract public attention.
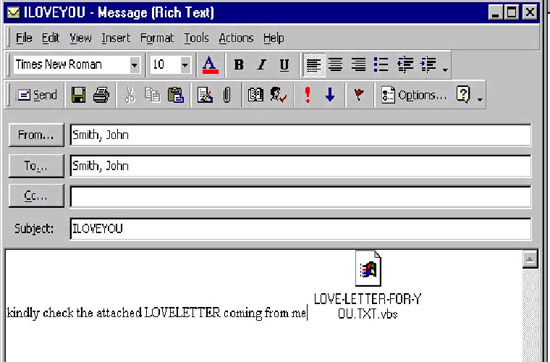
ILOVEYOU. A year after the Melissa virus devastated the Internet, a virus called ILOVEYOU from the Philippines caused a "cyber storm" . Like the previous virus, the virus takes the form of a worm, a standalone program, capable of duplicating and spreading itself through emai. The theme of the email says that this is a love letter from a mysterious fan. And the attachment is the virus. This virus has caused losses of about $ 10 billion.
Virus Klez. Klez virus marked a new development trend of computer viruses. It started raging at the end of 2001, and its variants have spread on the internet for several months. The Klez worm, after infecting a computer via an email message, duplicates itself and sends it to a list of friends in the victim's directory. Some variants of this virus also prevent the computer from functioning. Depending on the variant, this virus acts as a normal virus, a worm or Trojan virus. It even makes the antivirus software impotent.
Code Red and Code Red II. The two worms appeared in the summer of 2001. Both attacks the Windows 2000 and Windows NT operating system vulnerabilities. Meanwhile, computers running this operating system will receive more information than it can handle and it starts overwriting nearby memory. The Code Red worm kicked off an attack on the White House website servers. All infected computers will simultaneously connect to the White House web servers, causing it to be overloaded. Code Red II infected computers will not obey the host commands because it has opened a back door to the computer's operating system, allowing access and control of remote computers. The person who launched the virus can access all information from the victim's computer and even use infected machines to commit crimes.

Nimda. The virus also appeared in 2001. Nimda is a virus worm. It spread very fast on the internet, and it took only 22 minutes after it appeared, it was ranked at the top of the viruses that caused the recorded attacks. The main goal of this virus is internet servers, causing internet data transmission to be congested. Nimda uses many methods to spread, including email. It also creates a backdoor for others to access and control infected computers.

SQL Slammer / Sapphire. Appearing since the end of January 2013, Sapphire has attacked web servers that spread quickly over the internet and has 'knocked out' many important systems: US bank ATM services, Seattle's 911 service. cut, Continental Airlines was forced to postpone several flights because e-tickets and check-in systems were broken. The virus has caused damage of about $ 1 billion.

MyDoom. This is also a virus worm, creating a backdoor that attacks the operating system of the victim computer. The first attack, the virus made the internet network congested. The second attack, the virus attacks search companies, like Google, making the search service very slow and even corrupted.

Sasser and Netsky. Programmers of this virus, a 17-year-old German youth named Sven Jaschan created these two viruses and launched them on the internet. Although there are different ways of doing things, the similarities in code have made experts believe that this is the 'work' of the same person. Sasser attacks the Microsoft Windows vulnerability but does not spread via email, instead it looks for systems with other vulnerabilities. It will join these systems together and guide them to download the virus. The virus will randomly scan IP addresses to find the victims. The computer will not turn off if no power is cut. Netsky virus spreads via email and Windows network, causing network congestion.

Leap-A / Oompa-A. The virus is intended to attack OS-based computers, an operating system that is often less affected by viruses. It uses the instant messaging program on iChat to spread through other Mac computers. After being infected with the virus, it will search on iChat's contact list to send the message, accompanied by an infected file, disguised as a JPEG image.

Storm Worm. It was first discovered at the end of 2006. This is actually a malicious program. Its variants trick victims into downloading applications from fake links. The virus launcher regularly changes the subject of the email to keep up with the event stream. Storm Worm is considered one of the worst attacks of the virus for many years.
- The most dangerous computer viruses of the time
- The US removed the ban on fundraising for research on
- In the plethora of deadly epidemics, what is the most dangerous virus in history?
- Detection of new dangerous influenza viruses
- Top 10 most dangerous viruses in November
- Video: Dangerous germs hidden in Arctic ice are melting
- Why are more and more new viruses threatening humans?
- Warning of dangerous viruses transmitted from monkeys to humans
- More and more viruses are dying around the world, and the reason is not pleasant at all
- Computer virus appearances can
- Top 10 most dangerous viruses in June 2006
- Discover 18 strains of virus originating from mice
 The 11 most unique public toilets in the world
The 11 most unique public toilets in the world Explore the ghost town in Namibia
Explore the ghost town in Namibia Rare historical moments are 'colored', giving us a clearer view of the past
Rare historical moments are 'colored', giving us a clearer view of the past The world famous ghost ship
The world famous ghost ship