The biggest security threats in 2007
The online world is becoming more insecure, dozens, or even hundreds, of viruses and malware (malware) created every day, causing great damage to users. Under these circumstances, controlling your behavior online as well as understanding the rules and practices of malware will help you reduce unnecessary damage.
Threatening number 1: IE
Leading the list of 'bombarding' security goals in most recent reports of the FBI and SANS Institute is Microsoft's Internet Explorer browser. The reason: is the most widely used browser today, IE gives hackers huge amounts of revenue if they exploit the vulnerabilities of this application.
The source of security problems in IE is Microsoft's ActiveX technology, which allows websites to run executable programs on the PC through the user's browser. Patches and patches, including Windows XP SP2 and most recently IE7, made ActiveX more secure but unfortunately there are more and more vulnerabilities that allow malware to overcoming the security features, plus the curious fact of computer users, the improvement of ActiveX is not worth it. The good news is that with the exception of some restrictions (such as not being able to access Microsoft's Windows Update page), you can still use IE to browse the Web effectively without the need for ActiveX features.
To disable ActiveX in IE6 and 7, go to Tools > Internet Options > Security > Custom Level > Run ActiveX controls and plug-ins > select Disable (see Figure 1). Click OK > Yes > OK to close the dialog box. To enable ActiveX on a known and secure site, go to Tools > Internet Options > Security > select Trusted Sites > click Sites , and enter the site address in the dialog box and click Add . Uncheck the Require server verification (https: / for all sites in this zone , then click Close and OK .
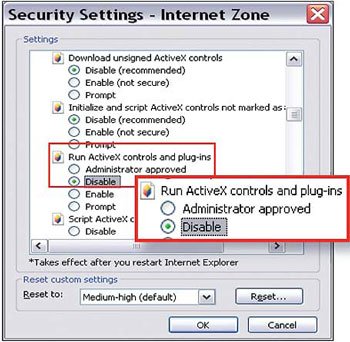
Figure 1
If you leave ActiveX enabled, you will quickly encounter dangerous sites (installing malware) and e-mail attachments that require installing ActiveX controls on the system. Unless you are 100% sure that these drivers are safe and legal, they will be installed, otherwise cancel them.
You must regularly update Windows and your browser to minimize the risk of security regardless of whether the default browser can be IE, Firefox, or Opera. To upgrade Windows XP, go to update.microsoft.com (must use IE to access this page - a popular form of Microsoft?) And install Service Pack (SP). ) 2 if your computer doesn't have this upgrade yet. Next select Start > Control Panel > System > and click Automactic Updates tab. Select the ' Automatic (recommended) ' mode if you fully trust Microsoft. Select the ' Download updates for me,' but let me choose when to install them 'option if you only trust Microsoft. And select ' Notify me but don't automatically download or install them ' mode so you can decide whether or not to install the upgrade.
If you feel that IE6 is too boring, upgrade to the new version - IE7 (ActiveX security has improved). In addition, there is another better way to reduce the security risk from ActiveX is to download and install another browser, and then configure them to be the default browser on the system. In this case, Mozilla's Firefox is considered the best alternative to IE. However, the popularity of Firefox has attracted the attention of hackers and the vulnerabilities of this browser are gradually exposed. Although no software is absolutely secure, many experts believe that Opera is still the best browser with a higher security index than IE and Firefox.
Threatening No. 2: Phishing online and identity theft
In fact, you may have been a victim of phishing. This type of attack is not new but still a very successful fraud, as evidenced by the increasing number of phishing victims in the past. The beginning of this scam is that you will receive a fake notification from a bank, PayPal, eBay, or other online accounts. Accordingly, this notice requires you to confirm the information by providing your username and password, credit card number, bank account information. You are often asked to click on a link to access the bank's website (actually a fake) to report information.
When prey has been bitten, phishers will collect the victim's data, then sell it to someone who needs to buy it or use it to withdraw money from the user account. Hackers often create a dangerous website, only slightly different from the real website (such as www.amazom.com instead of www.amazon.com in the hope that users do not notice when accessing.
It is possible that you have ever known the bank's regulations never to send customers e-mail asking them to log-in to their accounts, but most messages seem to be sent from organizations. finance is all in the form of 'phishing'. So it is better that you do not open them and do not click on any links in this message. If you are worried that the bank is trying to contact you to report a problem, open the website (enter the address) of that bank and log in directly to your account; or better yet, pick up the phone and call the customer service staff to ask for information.
If you find suspicious signs from an e-mail sent to you, or websites visited (to report personal information), you should notify the authorities or the bank to stop. Often phishing sites are not long, they only appear in a few days and then disappear after completing the task that its owner created.
Both IE7 and Firefox 2 are equipped with new anti-phishing features, which can compare links with databases of known phishing sites before displaying the site. Particularly IE7, the time to install this browser will last a little longer if users choose phishing filter during the setup process. To enable this feature, go to Tools > Phishing Filter > Turn on Automatic Website Checking > and click OK .
Meanwhile, the phishing filtering feature of Firefox 2 is enabled by default, but it downloads a static list of phishing sites to analyze and reconcile. To use Google's alternative Phishing Protection service, go to Tools > Options > Security > and select ' Check by asking Google about each site I visit ' (Figure 2). Note that you will have to accept the service provider's license agreement (here is Google).

Figure 2
Many security programs and firewalls are equipped with protection against identity theft. This function will control the flow of sensitive data (passwords, credit card numbers, ID numbers .) transferred from the computer and will conduct unauthorized behavior.
Threatening No. 3: Malware
The creators of viruses, spyware, and advertising (adware) always innovate on how to "market" and infiltrate your computer for the purpose of stealing information, destroying data. whether or not you use your PC as an attack pedal to another computer. The following steps will help you keep yourself safe from these risks:
Think carefully before clicking: Attachments with .exe, .com, .bat, and .scr extensions as well as some document files are attached with script code such as: .doc, .xls . can be invaded Enter directly into your computer with a single click. However, there are now many e-mail programs that prevent users from accessing attachments with executable files (.exe, .com .).
Using spam filtering features: Although some malware tries to break into computers through a browser, e-mail is still considered the main resource and the biggest target of this type of software. this. Installing a spam filtering program will help you reduce the risk of triggering malicious scripts attached to your received messages.
Upgrade antivirus software: Keep the antivirus program running on your computer after it has run out of time is worse than you do not use antivirus software. Because then, not only do you not update the new upgrade (virus identification database), but also the opportunity for malicious software to exploit the known vulnerability in the antivirus program. If your computer is required to run copyrighted programs, you should use the free antivirus program AVG Anti-Virus (www.grisoft.com).
Use more options: You can only install and use an antivirus program at a time on your computer because their real-time scanning engines will conflict with each other. If you suspect the effectiveness of antivirus software on your computer, use a free online virus scanner, such as ActiveScan (see Figure 3) of Panda Software (http:///www.pandasoftware. com / products / ActiveScan.htm) or Trend Micro's HouseCall (http://housecall.trendmicro.com/).

Figure 3
Kidney while downloading: Any program that you download and run on the system can be harmful to your computer, it can create a mechanism for intrusion or a springboard to attack the computer. other. You only download software from proven sources of security. These sources when the software is uploaded to the site they have scanned for malicious software in advance.
Using multi-directional firewalls: Windows XP and Vista are all equipped with firewalls that block attacks from outside. In Windows XP SP2 or later versions, the firewall feature is enabled by default. However, to increase the level of security you should block unwanted connections sent from your own computer (Windows XP does not have this capability, you must install your own firewall software), in case of If malware spreads spam or tries to connect to a remote server.
Meanwhile, Windows Vista can prevent connections from inside, but configuring it is not easy for most Windows users. Instead, you can use one of the many free multidirectional firewall programs like ZoneAlarm Free (Zone Labs - http://www.zonealarm.com) or Outpost Firewall Free (Agnitum - http:/// www .agnitum.com). Most commercial security software packages integrate firewall programs.
Use a spyware removal program: Spyware, adware and some browser cookies can slow down the system of term, annoying and keep track of your online activities. Antispyware applications have the same way of working as anti-virus software, which helps detect and remove unwanted programs on your PC.
PCWORLD rated Spy Sweeper 5 (http://www.webroot.com - $ 30 / year) is a good candidate for spyware prevention.
Upgrade Windows XP: SP2 will make Windows XP much safer, but the operating system also has many security holes exploited by hackers. Meanwhile, Windows Vista's new user access control function will ask for your comments before activating any program, helping to reduce the risk of automatic malware attacks (from the web) on your computer. of you, although some vulnerabilities have been discovered in this operating system. And Mac OS and Linux have a very strict protection mechanism for activating the program. Therefore, these two operating systems are rarely the target of hackers.
Van Han
- 5 biggest Internet security threats
- He worries about the solar storm
- The biggest threats can wipe out humanity
- Botware raged in August
- Security tool all in one
- Microsoft introduced a fee-based security service
- Security tools are available for Vista
- Security threats from ... Xerox printers
- Cisco acquired security company IronPort Systems
- McAfee is sued for patent infringement
- 'Network weapon': Indispensable in the UK arsenal
- 5 potential threats to destroy humanity
 What is the Snapdragon SiP chip?
What is the Snapdragon SiP chip? How to create a yellow circle around the mouse cursor on Windows
How to create a yellow circle around the mouse cursor on Windows Edit the Boot.ini file in Windows XP
Edit the Boot.ini file in Windows XP 3 ways to restart the remote computer via the Internet
3 ways to restart the remote computer via the Internet