Information Security Department instructs how to handle emergency WannaCry extortion codes
The Information Security Department has issued guidelines for emergency handling of WannaCry extortion codes for users as well as organizations and businesses to avoid damage caused by this malicious code. Vietnam is currently on the list of 20 countries attacked by this malicious code.
The Department of Information Security (Ministry of Information and Communications) said that currently, malicious code named WannaCry exploits some vulnerabilities in the Windows operating system to attack computers with the goal of encrypting data for ransom, affecting many organizations and individuals on a global scale. Department of Information Security - Ministry of Information and Communications instructs organizations and individuals to implement this emergency handling method as follows:
Specifically, for individuals who need to make immediate updates to the version of the operating system Windows is using. Particularly for computers using Windows XP, use the latest update specifically for this task at: ttps: //www.microsoft.com/en-us/download/details.aspx? Id = 55245 & WT. mc_id = rss_windows_allproducts or search by update keyword KB4012598 on Microsoft's home page.
Individuals also need to update the programs Antivius is using right away. For computers without Antivirus software, install and use a copyrighted Antivirus software immediately. The Information Security Department recommends that users be cautious when receiving email with attachments and strange links sent in emails, on social networks, chat tools .
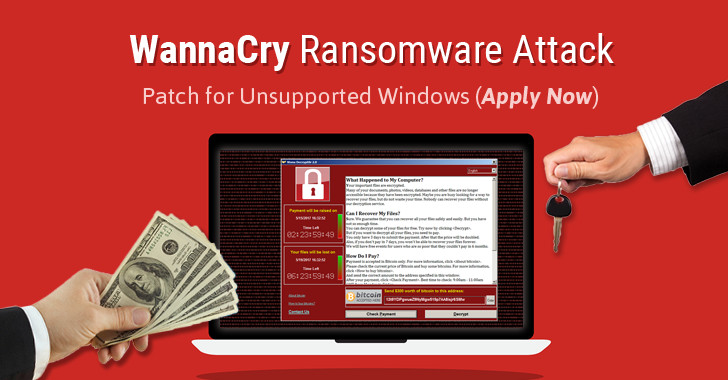
Users are cautious when receiving email with attachments and strange links sent in emails, on social networks, chat tools .
Users need to be cautious when opening attachments even when received from familiar addresses. Use online or copyrighted malware testing tools on your computer with these files before opening them. The user does not open paths with an .hta extension or an unclear path, shortened links and concurrently store important data (backup).
For organizations and businesses, especially for system administrators, it is necessary to immediately check the servers and temporarily block (services) the services using ports 445/137/138/139 . Organizations and businesses need to take measures to update early, appropriate according to each specific for the organization's windows servers. Create snapshots for virtualized servers in anticipation of being hacked. Organizations and businesses must take measures to update workstations using Windows operating systems. Update the database for the current Antivirus Endpoint servers. For systems that do not yet use these tools, it is necessary to use Endpoint software with the latest copyright and updates immediately for workstations. Organizations and enterprises take advantage of the information security solutions available in organizations such as Firewall, IDS / IPS, SIEM . to monitor, monitor and protect the system during sensitive times. this. Update updates from security vendors for available solutions. Also, prevent and monitor domains that are being used by the WannaCry malware, to identify infected computers in the network to take timely measures:
http://www.iuqerfsodp9ifjaposdfjhgosurijfaewrwergwea.com/. This domains have been sinkholed, the Information Security Department will constantly update this list on the website.
Organizations and businesses consider blocking the use of Tor in the network and take measures to store (backup) important data right away. Organizations and businesses warn people and take measures as mentioned above for users. The Information Security Department also recommends organizations and businesses to immediately contact the authorities as well as organizations and businesses in the field of information security to be supported when needed.
- Not only blackmail, WannaCry malicious code can be deadly
- Video: WannaCry's terrifying spread rate
- 5 things you need to do immediately to prevent WannaCry malware
- Overview of Wannacry virus - The world's most dangerous malicious code
- The appearance of new extortion code spread quickly
- Microsoft instructs security of personal information
- Check out a computer literacy company
- The first aid for burns
- Little interesting things about QR codes
- The US tested a digital emergency warning system
- 10 most dangerous malicious codes in March 2007
- Why is information insecurity still happening frequently?
 What is the Snapdragon SiP chip?
What is the Snapdragon SiP chip? How to create a yellow circle around the mouse cursor on Windows
How to create a yellow circle around the mouse cursor on Windows Edit the Boot.ini file in Windows XP
Edit the Boot.ini file in Windows XP 3 ways to restart the remote computer via the Internet
3 ways to restart the remote computer via the Internet